Chris Valasek is the Keynote speaker on October 21, 12pm at SecTor Security Conference.
While hacking a car almost always requires physical access,
it won’t be long before it doesn’t.
Consider this scenario: a virus is accidentally downloaded onto a driver’s phone, who unknowingly pairs it to his car, now the infection is inside the vehicle, where the Bluetooth and brakes run on the same network… what’s the defence?
How do you mass-update the software in tens of thousands of cars? It can costs millions just for an automaker to mail a “come in and get updated” letter to its customers.
As vehicles become more computers-on-wheels than cars, the act of securing them should be a priority for automakers, yet there’s an absence of information on this topic.
Here’s a rare opportunity to hear from a bleeding-edge expert at this year’s SecTor, Canada’s premier IT security conference.
Christopher Valasek is a pioneer in automotive security. He serves as Director of Vehicle Security Research at IOActive, one of the first companies to specialize in automotive security.
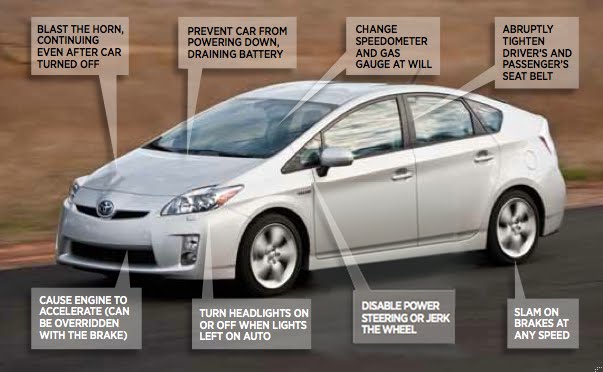
He’s not just a theory guy, Chris is an actual practitioner. Remember last year when the headlines screamed “a Prius and Ford have been hacked!’ – that was him. If you’ve read anything in the news about car hacking, it probably contains a quote or citation to his work.
He’s not out to do bad and hack your product, or show up individual OEMs, this is a rare chance to hear from one of the good guys, plus – the added advantage of having a mind like this assessing your product, for free.
On October 21 at noon, Chris’ keynote presentation, ‘The Connected Car: Security Throwback’ , will demonstrate how present-day automotive security is like a hard shell with a gooey inner layer – protect the outside, but once inside, it’s a field day.
(photo via Forbes)
He’ll draw comparisons between today’s auto landscape and the early 2000s of the internet, when protection mechanisms were an afterthought. He feels automotive security is stuck in a hole in time, and that the same solutions used to secure the networks of 10 years ago, can be applied to today’s automotive security issues.
Because the more computers and code that go in to cars, the greater the odds of a mistake being made and someone like Chris finding it. Moreover, with the automotive production cycle being so long (2018 model years are now being finalized), a problem found today is going to be prevalent for some time.
Automotive industry types – is your product resistant against a cyber-attack? If you’re not securing the vehicles you’re producing, then they can be weaponized, and yes that sentence is intended to give you chills.
His keynote will include the opportunity to ask questions. Catch it at SecTor on Tuesday, October 21 at 12:00 – 1:10pm. Ticket information here
Blog tag = auto security
Meet me in this post