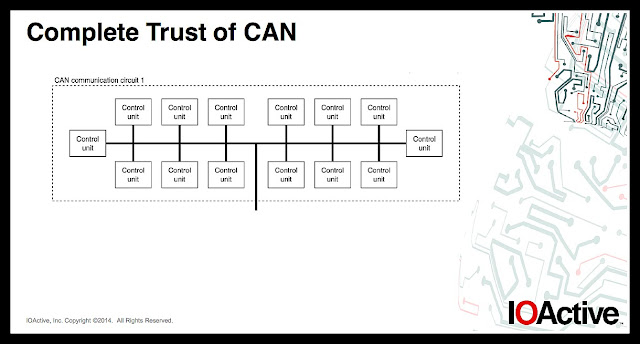
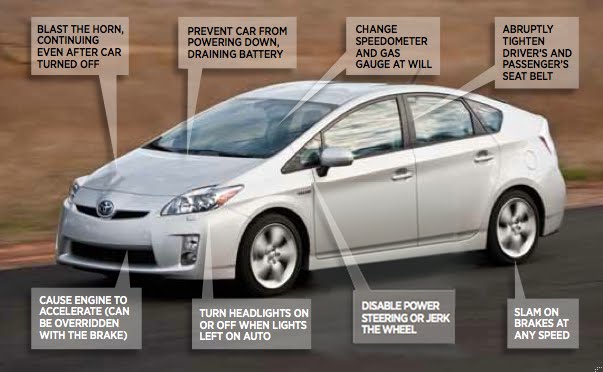
Real brief: the problem is cars operate on the CAN bus network, which was designed in the 1980s, when the internet didn’t exist. Learn about CAN here.
Speaking with Chris Valasek, physical access is still required to hack the car. For now. (I’d try coming in via Bluetooth.)
Read it online at Autonet.
Favourite line:
That’s how car hacking works: the system doesn’t ask where the message came from or who sent it, it just accepts and executes it.
Plus the ending, because it’s true.
To attack, it’d be more efficient to roll that newspaper into a baton, than go after the target’s car.
***
Back to ‘Keri on Driving’ – Index
Blog tag = auto security