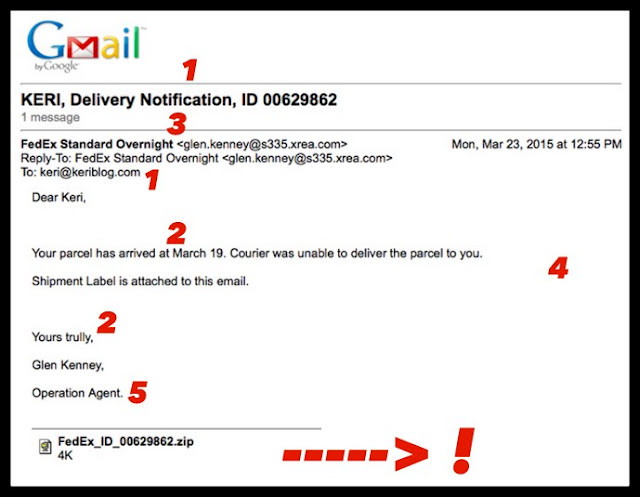
It arrived in my Gmail earlier this week. How many clues can you spot?
I’ll give you the first two, it’s unfair not to…
1 – I didn’t order anything, and if I had, it wouldn’t have been using that email address.
2 – terrible spelling and grammar, FedEx would never
3 – the big red flag – a non-FedEx email
4 – the absence of information, there’s no links, tracking number…
5 – Operation Agent. I like the name though
As far as phishing emails go, this one’s obvious; see the LinkedIn one for a more sophisticated example here.
—-> ! Know what’s impressive though? —-> !
The attachment made it through Google’s security checks and filters. Nicely done guy.
That’s why never let downloads open automatically – more here.
And see how small it is? 4K, tiny. Doesn’t take much to mess your machine up.
Stay sharp out there.
Blog tag = Phishing