TELUS has released their 6th annual study of Canadian business security practices.
The report focuses on which best practices businesses have in place, that go beyond just compliance (as in, the bare minimum forced on you by the government.)
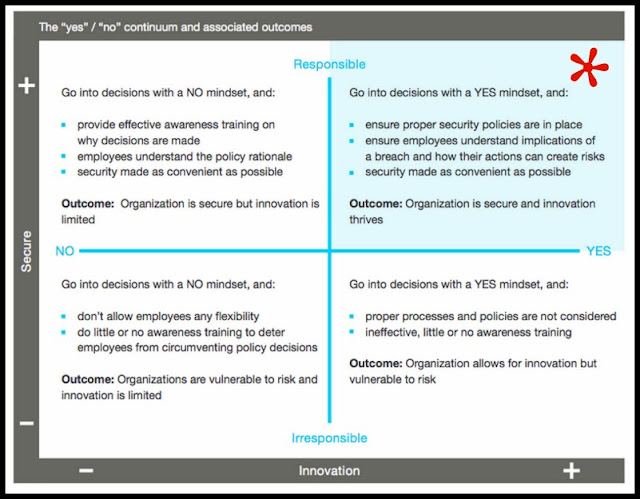
Ideally, your business is in the quadrant with the *.
How does your small business compare? Take this test to find out.
Give yourself a score between 0-7 (0 being terrible, 7 being excellent), then compare how you operate to other Canadian businesses.
Do you…
1 – monitor and/or have rigorous procedures to act on new threat information
2 – understand the security drivers impacting your business
3 – conduct regular security awareness training for employees
4 – involve security early and throughout the development of new infrastructure/systems
5 – communicate social media policies to their employees
6 – have and/or execute on a comprehensive mobile security strategy
7 – conduct enterprise mobility security testing and Threat Risk Assessments (TRA)
Now compare:
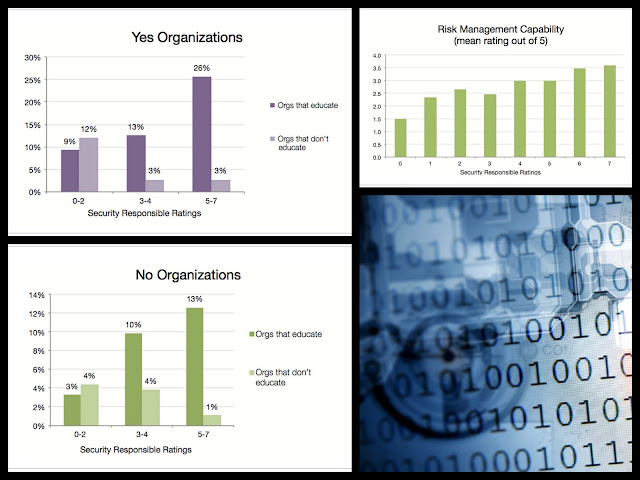
The more “security responsible” companies have: less breaches, retain staff longer, better managed risk, and are positioned better to take new risks (side-note from me: they have better business karma, because accepting a credit card and being careless and lazy about it is terrible.)
And ideally, you have ongoing employee training sessions, because the human is always the weakest link.
Note:
This is an excerpt from my interview with Hernan Barros, Directory of Security Solutions at TELUS, and Walid Hejazi, Associate Professor, Rotman School of Management, University of Toronto, about their new study, the 2014 TELUS-Rotman IT Security Study.
The study is in its 6th year, and TELUS remains the country’s only telecom to proactively study security, and this is the only Canadian study this in-depth on a single country.
How it was conducted: 400+ security professionals were surveyed in the 2nd half of 2013, looking for both qualitative and quantitative data on how companies are executing their security strategies. Respondants were Private 48%, Government 23%, Publicly Traded 20%, and Non-profit 9%.
Blog tag = TELUS Security