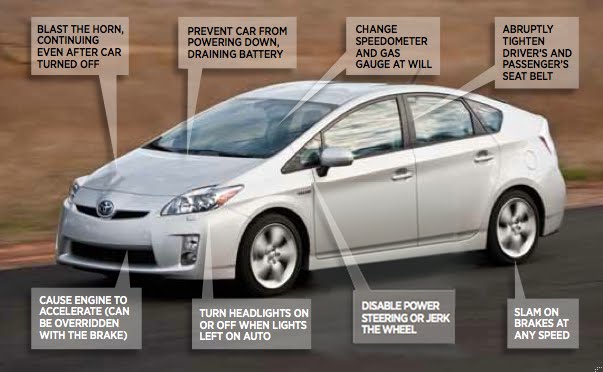
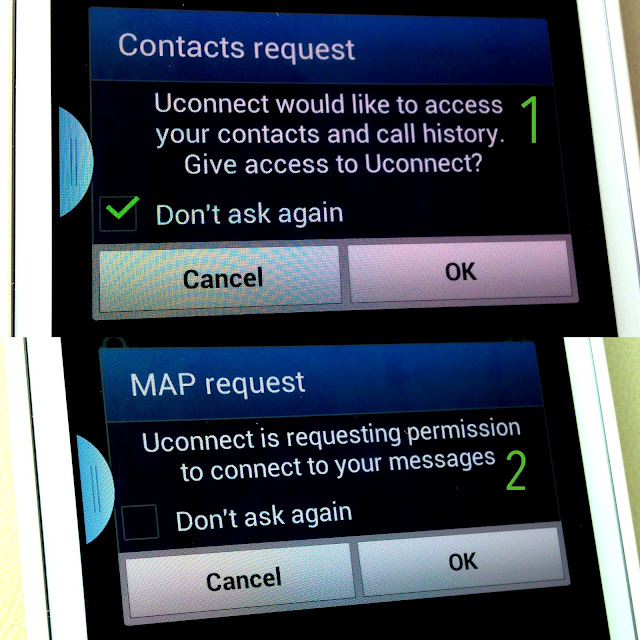
A group of security professionals have formed “The Cavalry“: dedicated to improving collaboration between the cyber security and automotive industries.
Because what if things like adaptive cruise control, electronic braking and stolen vehicle recovery technology could be used nefariously? What if all Toyotas in Canada were instructed to go left next Tuesday at 1pm? Like that.
Specifically, they’re proposing a Five Star Automotive Cyber Safety Program:
1 – Safety by Design
2 – Third-Party Collaboration
3 – Evidence Capture
4 – Security Updates
5 – Segmentation & Isolation
Why I signed:
Sign it too, here.
Non-security nerds: I know this stuff can seem shadowy and strange, with a name like “The Cavalry” and a blank profile pic, but in this particular case it’s okay, I know one of the guys in real life; I signed with my real name, not Blog.