I’ve harped on you for years via social media, “stay off airport WiFi, it’s dangerous and even the best guys don’t connect to it”.
When I travelled to Arizona two weeks ago, sitting at the terminal I was like, “okay fine, I have to wipe my phone soon anyway, and should demonstrate why I keep harping”.
I connect to the terminal’s free network.
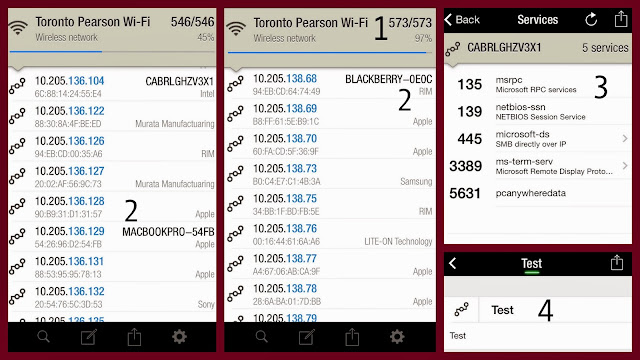
Using an app on my phone, I scan the network.
1 – there are 573 devices connected to the network
2 – the brand of each device is displayed
3 – I can choose to see what each device is doing
4 – I can pick one device and track it! I assign it the name, “Test”
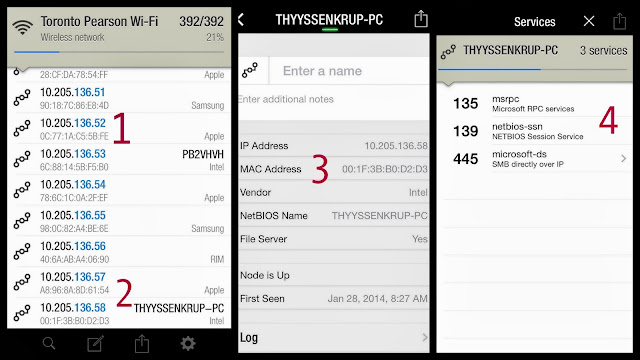
1 – listed are the IP (like an address) and MAC address (like a serial number) of all connected devices
2 – let’s see what’s happening with THYSSENKRUP-PC
3 – that’s his IP and MAC address, of his Intel PC
4 – the numbers on the left are his ports, and what traffic is going in/out on each
* – this traveller has his business card taped to his laptop.
The Attack
A business traveller has connected both his phone and laptop, he’s working away. The attacker notes his brand of device, the device’s name, MAC and IP address, and what is happening on which ports. Added bonus is the business card taped to the laptop.
The attacker does some social media mining, then a week later, the traveller gets a phone call.
“Jimmy hi! Karl from IT here. Look, there’s a bit of a meltdown happening at HQ, sorry but this is urgent, you were at Pearson airport last Tuesday, right?
You’re on a Blackberry, MAC address 00:1F:3B:Bo:D2:D3, and were connected to our Microsoft Exchange server, right? Yup, look, we have a compromise here, and I’m going to need your access to your laptop…”
***
An elaborate example, because really, someone skilled now has enough information to breach Jimmy’s system, with neither the laptop lid business card, or a phone call.
The Defence
Use your phone (via USB, not Bluetooth) to connect to the internet. Reduce the attack surface.
The Better Defence
Just don’t.
If you must, avoid entering any passwords, and certainly no banking or credit card numbers.
(see also: Protecting your Phone in an Uncertain Environment)