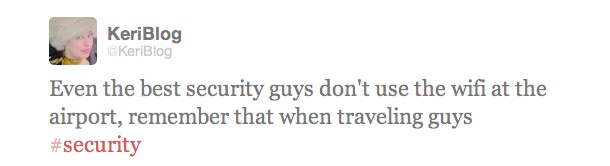
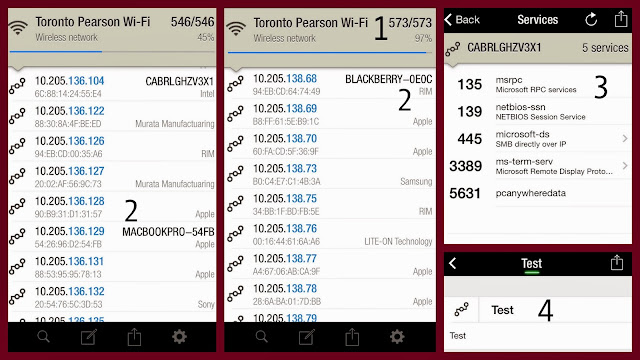
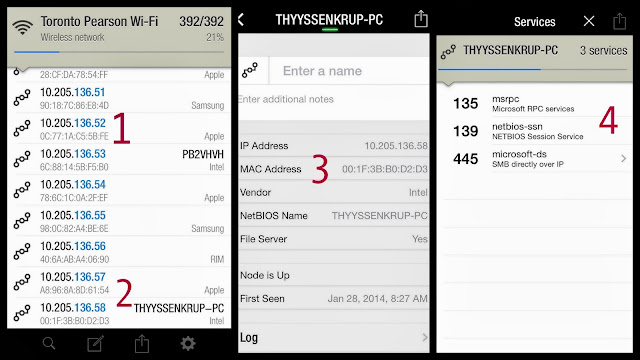
It’s a screenshot of my iPhone settings I took while in the USA last week.
Answer – Personal Hotspot
Canada telecoms allow us to connect our laptops via our phones, to Hotspot.
The States isn’t into them. Instead, they use MiFis – a stand-alone device that looks like this – 2nd last photo.
Remember: you are legally responsible for anyone who uses your HotSpot.