That’s one of the oldest saying in security, because it’s true.
Thinking you are going to be forever immune is delusional.
Do you not lock your front door? Lock your car when you park it downtown? Take a different walking path at night than during the day? Why would online actions require less diligence and care?
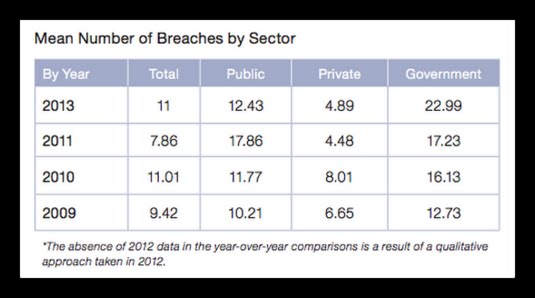
Here’s the mean number of breaches to Canadian companies, over the last 4 years.
Note that none of them are 0.
If you are a small business owner:
You have a responsibility, especially if you are accepting people’s credit card numbers. Because you may be more of a target than you realize… think like an attacker: is it easier to go after 1 large business, that likely has security systems and staff in place? Or 10 smaller businesses, who probably have no clue and are lazy about protecting their assets?
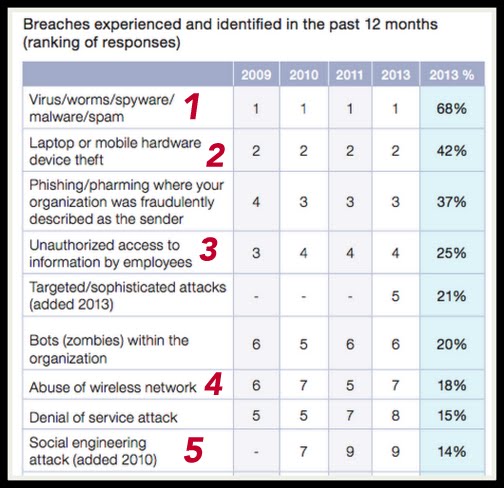
The type of breaches Canadian companies experienced last year.
1 – one careless click, on one stupid link…
2 – how old-fashioned! Never leave your laptop unattended
3 – from the inside…
4 – lock your WiFi network. And change your router password too, how to here
5 – the counter to this attack is listening to your gut. Blog tag = social engineering
***
This is an excerpt from my interview with Hernan Barros, Directory of Security Solutions at TELUS, and Walid Hejazi, Associate Professor, Rotman School of Management, University of Toronto, about their new study, the 2014 TELUS-Rotman IT Security Study.
More about that here.