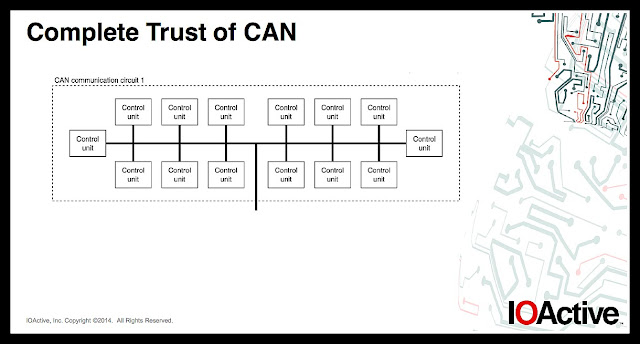
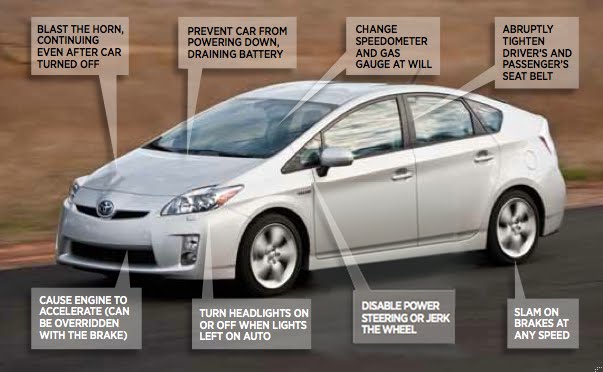
Screenshots from the Black Hat presentation about the first remote hack of a passenger vehicle – a 2015 Jeep Cherokee (more here.)
It was these guys – Charlier Miller and Chris Valasek.
2 Biggest Takeaways for the Average Driver
1 – the attack they released no longer works
As of publishing of this post, the attack stopped working because Sprint closed the port they were using to enter the car (nice Sprint.)
If you own a Chrysler and were part of the 1.4 million recall, breathe a bit easier.
2 – update your car
This Jeep thing is a wakeup call – if your automaker issues an update, make it a priority. The industry is still in its infancy, the update will probably be inconvenient “pick up a USB from the dealership” DO IT.
Be mindful about how you connect your car to the internet (please never pair your car to public WiFi.)
From Black Hat 2015.