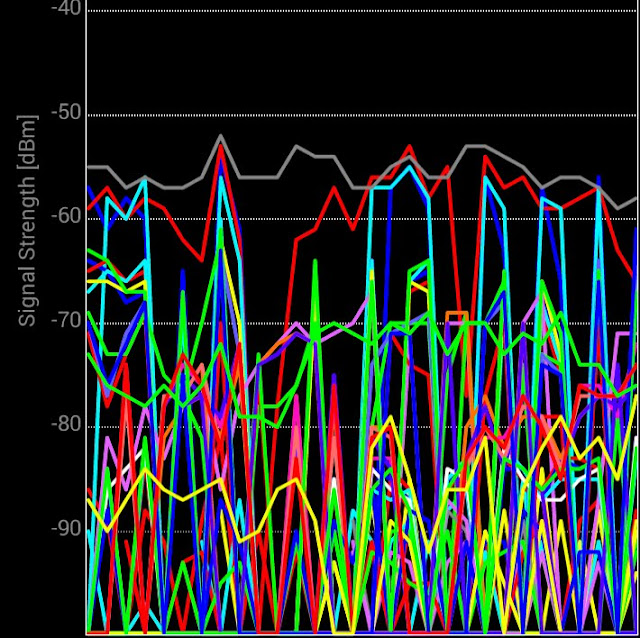
Pretty eh.
And unsafe – airport WiFi is considered
the most dangerous network in the world.
Why? Read these 2 posts – here’s a possible attack, and the time when I was compromised using it at ORD Chicago.
How to Protect Yourself
Don’t connect to it.
But you have to get online?
Tether your phone, via USB, to your laptop.
Not possible? Then do this:
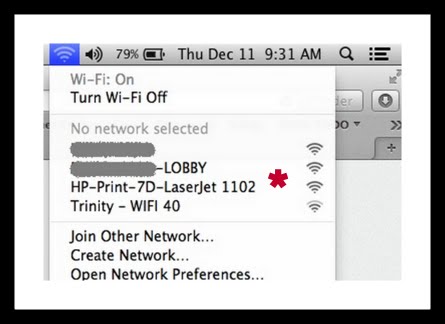
– check the network name and verify it’s actually the airport, and not someone spoofing it. Example: FreeWiFiAtPearson is probably fake
– only visit sites using SSL (the address bar will have an S in it – httpS://KeriBlog.com – like that)
– turn on your firewall
– never enter any logins or credentials; banking from an airport WiFi connection is practically begging for it
– use a VPN – Virtual Private Network
– turn off WiFi on both phone and laptop when not in use
Another screenshot of airport WiFi.
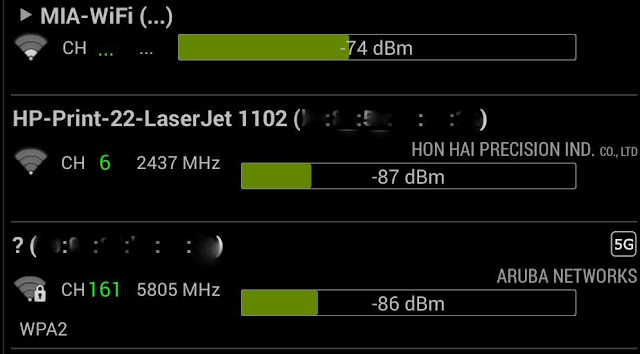
WAIT. This just hit me… could that printer be a honeypot?
That’s in Miami, and seems odd to permit a printer to be unlocked – ( why to always lock your printer here) – and like, if I was in charge of securing an airport I’d tell the vendors lock theirs…..
Blog tag = Wifi Security
Blog tag = Airports, because I love them