I’ve written about it at work, but this was my first experience using it in real life.
For more details, read my column from February.
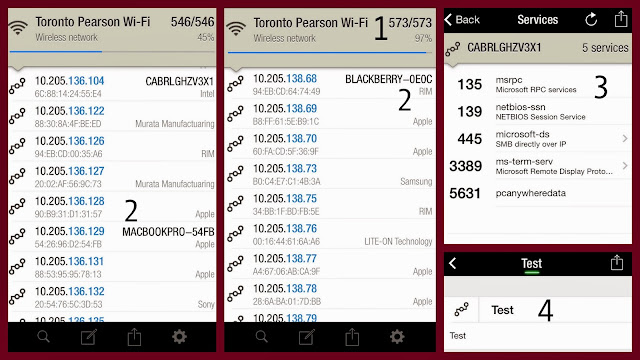
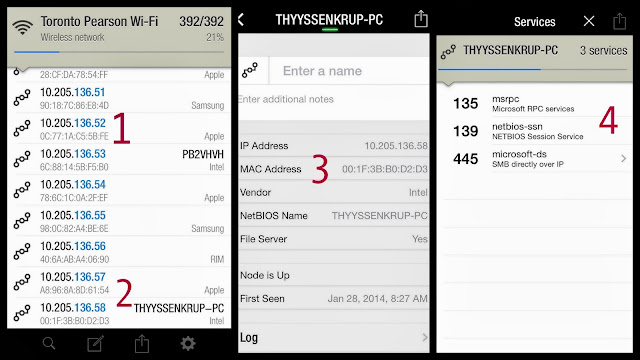
1 – it functions much like the Hotspot feature on a cel phone: car broadcasts WiFi > passengers connect to car > go online
Securing your car will be similar to securing your home WiFi.
2 – choose this option, WPA2
3 – don’t bother with WEP
4 – if you check this, please leave my blog
Because remember, you are legally responsible for Hotspot users.
Blog tag = WiFi Security