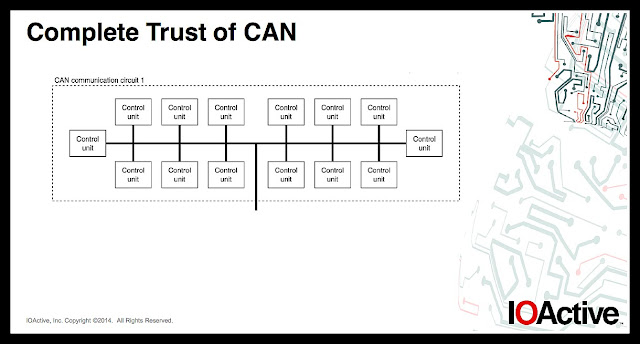
Set of lock picks
The L-shaped ones on the right are “torsion wrenches”. Use one of those simultaneously with one of the “picks” on the left.
A lock pick gun
It automates the above process, and while often seen in movies, it’s not that seamless.
It’s way noisier than you’d like it to be, and causes more damage to the lock than picks, leaving evidence of your presence.
(always be mindful of where you leave fingerprints.)
Spotted at SecTor 2014